Business Security
Firewall Solutions
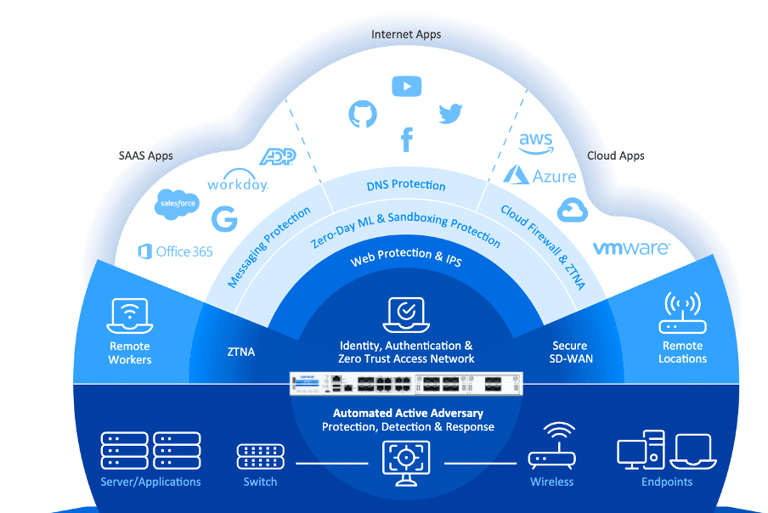
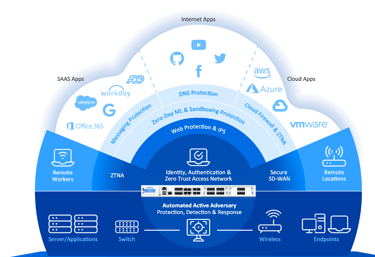
We provide affordable, comprehensive protection tailored for small businesses through a low-cost annual subscription. For medium-sized businesses, our solution expands with additional modules to meet evolving needs. Every firewall includes Central Cloud Management, reporting tools, and zero-touch deployment. Our solutions support all deployment models—hardware appliances, virtual machines, software, and cloud-based as a service setups.
TLS Inspection: Supports TLS 1.3
DPI Engine: Enables real-time deep packet inspection
IPS: Next-generation intrusion prevention
Active Threat Response
Synchronized Security: Automatically detects and isolates threats
Clientless VPN: HTML5-based access
SSL VPN
Reporting: Comprehensive network and threat analytics
Network Protection
Web Control: Manage access by user, group, category, URL, or keyword
Web Protection: Defends against the latest online threats
App Control: Regulate applications by user, group, category, risk level, and more
Synchronized App Control: Detect and classify applications
Synchronized SD-WAN
Reporting: Detailed web and application activity reports
Web Protection
Zero-Day Threat Protection: Combines machine learning and sandboxing for file analysis
Machine Learning: Utilizes advanced deep learning models
Cloud Sandboxing: Performs dynamic runtime analysis of suspicious files
Reporting: Provides comprehensive threat intelligence and analysis reports
Active Threat Response


Zero-day Protection


Core Features
SD-WAN and VPN: Xstream SD-WAN, IPsec/SSL site-to-site and remote access
Zero-touch deployment: For new
firewalls from the cloud
SD-WAN orchestration: Point-and click
site-to-site VPN orchestration
Networking and SD-WAN: Wireless, SD-WAN, application-aware routing, traffic shaping
Central Cloud Management
Medium Business
Small Business
Firewall Policy: Rules Policy, Inbound Rules, Forwarding Rules, SNAT ,DNAT Security Defense: DoS Defense, Spoofing Defense, Anti-malware: Data Packet Inspection Depth, Scan Compressed Files, Virus Signature Library Intrusion Prevention: IDS/IPS, IDS/IPS IP Exception, Botnet IP Protection, Botnet Domain, Name Protection, Botnet IP/Domain name Exception, IPS Signature Library Content Control: DNS Filtering, Web URL Filtering, URL Category Filtering, Keywords Filtering, URL Signature Library, Application Filtering Rules, Override App Filtering Rules, App Signature Library SSL Proxy: CA Certificates, Source Address, SSL Proxy Exemption List, Security Log: Log List, E-mail Notifications, Central Cloud Management, VPN


AI and ML DPI engine, application identification, anti-malware, IDS/IPS and more...
Award-winning Unified Zero Trust (UTZ) Platform
One solution securing all your business endpoints and cloud workloads.
Prevents costly breaches before they happen, saving you up to 50% in potential downtime and recovery costs. Our automated protection keeps your teams productive while meeting strict compliance requirements - all through one easy-to-manage platform. It's the smart way to secure remote work, avoid ransomware disasters, and turn security into a competitive edge.
We cuts licensing sprawl by consolidating CNAPP, email, and web security into one platform, lowering total cost of ownership






ENDPOINT PROTECTION
EMAIL PROTECTION WITH SECURE EMAIL GATEWAY (SEG)
Proactive threat containment is vital for security and business continuity. Your assets - protected.
Advanced Threat Detection, Real-Time Monitoring, Automated Incident Response, Forensic Analysis, Threat Intelligence Integration, Big Data VirusScope Analysis
YOUR BENEFITS ARE:
Stronger security, Lower costs, Higher productivity, Scalable protection
Our AI-powered Email Protection stops zero-day threats by neutralizing malicious links.
Multi-Vectored Defense, AI/ML Detection, Anti-Spoofing, Advanced Malware Blocking, Granular Policy Controls
YOUR BENEFITS ARE:
Complete visibility & reporting, Guaranteed customer data protection, Prevention of financial losses, Fully managed 24/7 defense at predictable costs
WEB PROTECTION WITH SECURE INTERNET GATEWAY (SIG)
Cloud-based web filtering that blocks threats and restricts inappropriate content—set up in 5 minutes, zero maintenance.
AI-Powered Web Filtering, Content Control, On & Off-Network Protection, Customizable Policies, Real-Time Monitoring & Reporting, Bandwidth Optimization, Zero-touch deployment
YOUR BENEFITS ARE:
Value, Simplicity and Security
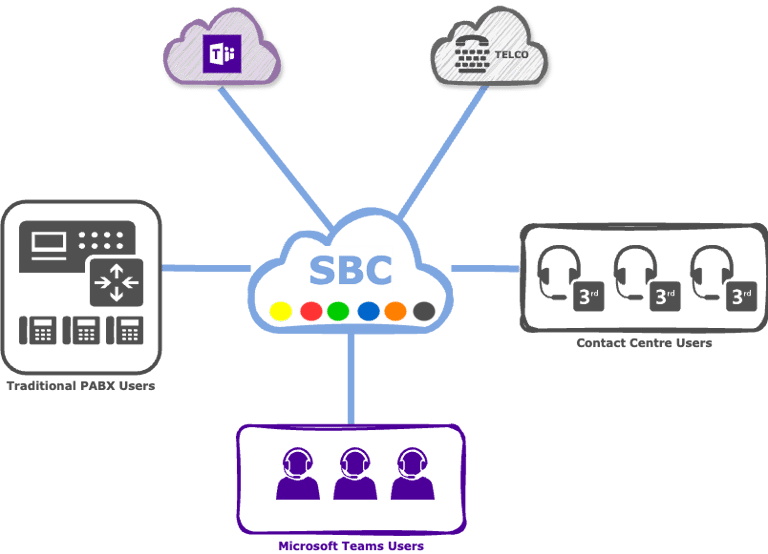
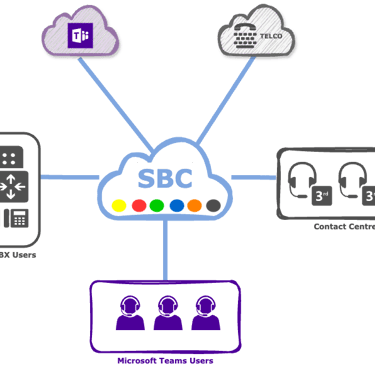
Session Border Controllers
Bridge the gap between traditional and modern telephony—facilitate transition to SIP with Cloud-native SBC as the Border Security.
Upgrade your underused Microsoft Teams with SBC-powered telephony—turn it into a complete, cost-saving calling hub and modernise your workplace
The Retirement of ISDN Services in Australia
Australia's ISDN phase-out mirrors the global shift to IP communications, as aging ISDN tech gives way to modern broadband-powered networks.
With Australia's ISDN shutdown in 2024-2025, businesses must switch to SIP/cloud telephony—SBCs ensure a smooth, uninterrupted transition


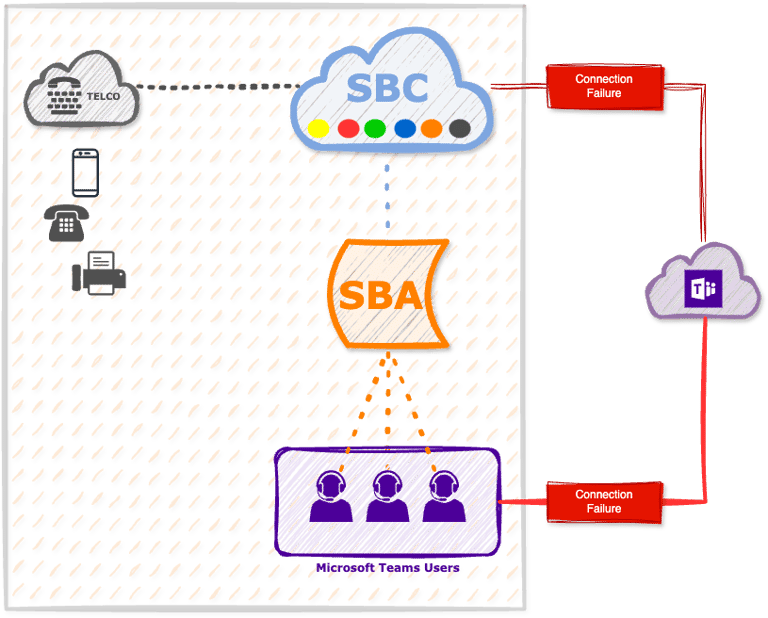
Survivable Branch Appliance (SBA)
Ensure uninterrupted voice communication for your offices, a resilient solution that keeps your business connected—even during network disruptions.
✔ Minimize Downtime – Maintain Microsoft Teams voice functionality during outages with automatic PSTN failover.
✔ Universal Compatibility – Works seamlessly with your existing telephony systems.
✔ Simple & Scalable – Low-maintenance solution with no complex hardware or installations.
✔ Grow with Confidence – Easily extend protection to additional branch offices as needed.
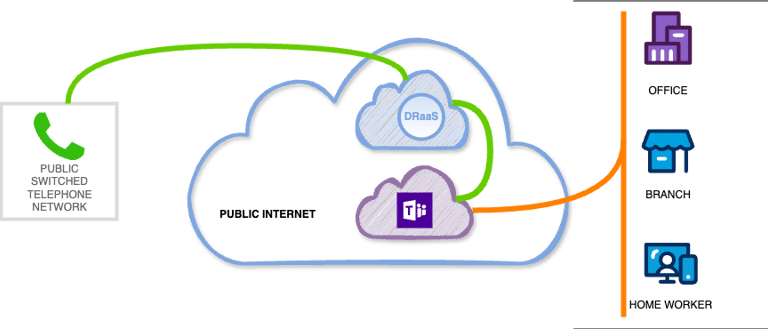
Enable PSTN calling in Microsoft Teams through your existing telephony infrastructure using cloud-hosted Session Border Controllers (SBCs). This solution eliminates PBX dependency while maintaining call quality, security, and compliance - all managed as a service. Scale flexibly, reduce telecom costs by 30-50%, and maintain business continuity with automatic failover, all within the Teams interface your users already know.
Direct Routing as a Service (DRaaS)
SIP Security
SIP-based voice services over IP networks face risks like eavesdropping, fraud, and DoS attacks. An SBC acts as a firewall for VoIP, protecting against threats like call hijacking and toll fraud through encryption, access control, and real-time traffic monitoring. By securing your SIP traffic, SBCs ensure safe, reliable, and private communications—just like a firewall safeguards your data network.
Key Protections:
✔ Blocks spoofing & fraud
✔ Encrypts calls & signaling
✔ Enforces strict access controls
✔ Monitors for threats in real-time


Facility Management Security Services
Transform your facility’s safety with our HD Intercom & Facility Control Station—a centralized solution for door access, video surveillance, intercoms, and building communications. Deploy our Full HD IP cameras for proactive, easy-to-manage security with crystal-clear monitoring. Our intercom and paging systems are perfect for offices, schools, healthcare, retail, and warehouses, ensuring seamless communication.
Integrate AI-powered video analytics to instantly detect faces, track movements, and locate vehicles across your camera network—enhancing real-time and retrospective security insights. With secure access control, manage building entry via audio/video intercoms, fully compatible with our ecosystem. Our technology doesn’t just protect—it boosts efficiency, safety, and competitiveness for smarter urban and enterprise environments. Secure more. See more. Stay ahead.
Facility Access Solutions
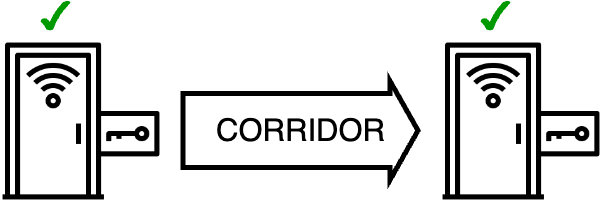

INTERLOCKING DOOR MORE
Enforces strict one-way access:
User authenticates via RFID/PIN
System verifies both doors are closed
Grants sequential entry with timed access
Perfect for high-security areas - prevents tailgating while maintaining smooth authorized access. Controlled entry, simplified.
TWO-DOOR CONTROL
Granular facility access:
Combinations of Door 1: Controlled via built-in RFID + PIN (local authentication) and Door 2: Managed by Wiegand input (3rd-party devices supported) - Multiple access methods:
Universal PIN (shared access)
Remote PIN (admin-controlled entry)
Private PIN/Card + PIN (high-security zones)
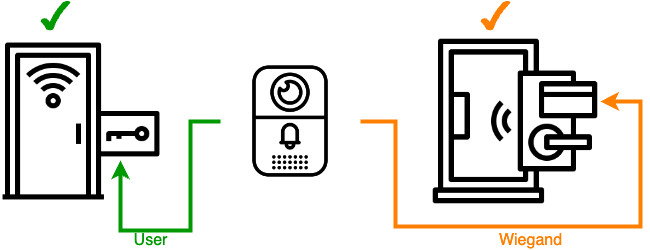

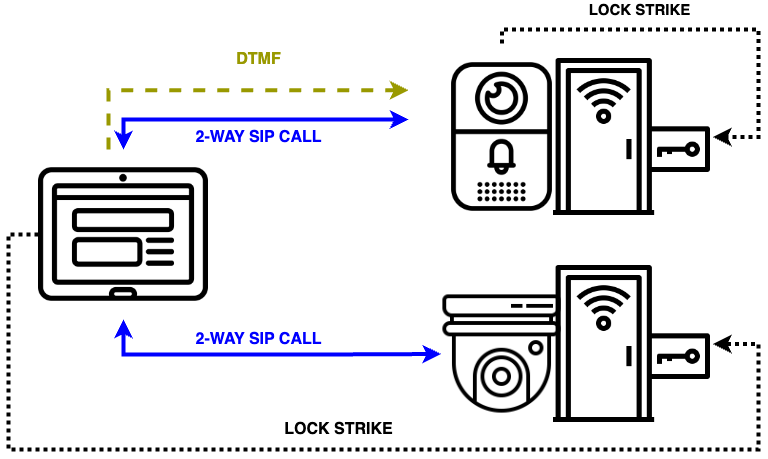
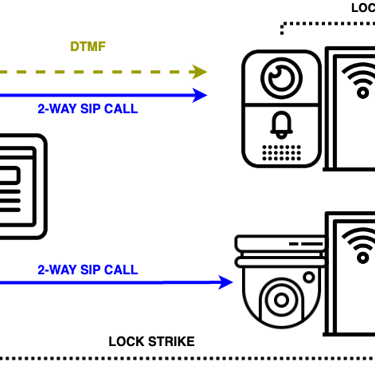
FACILITY CONTROL STATIONS
Versatile control with endless integration scenarios:
Support for latest smart building apps, IoT, automation and user-friendly interface.
Seamless Integration – Works with door stations, SIP cameras, 3rd-party doorbells, and standard door strikes
Smart Room Management – Monitor occupancy, reserve meetings, and adjust schedules in real time
Total Facility Control – Run Android 13 for lighting, HVAC, and smart office apps
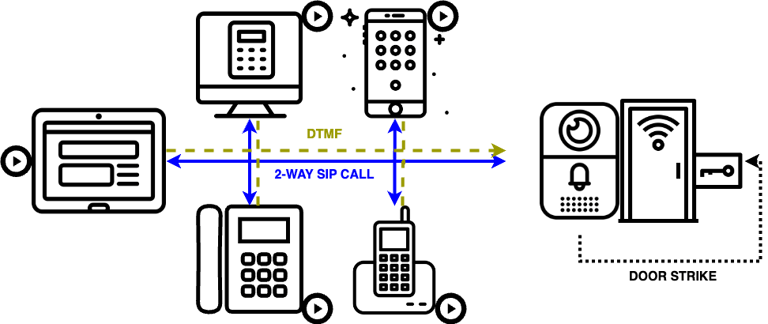
INTERCOM DOOR STATIONS
The Ultimate Access Control Starts at Your Door
Our industrial-grade Intercoms redefine facility security as the all-in-one solution for modern access control. Engineered for reliability, weatherproof and vandal-resistant.
Go beyond basic security with seamless integration across your entire communication ecosystem – control access from desktop phones, cordless DECT handsets, or our mobile UC client whether you're on-site or remotely managing facilities. Every interaction is recorded and tracked, transforming your entry points into smart security hubs that never sleep.
Video Analytics
SECURITY
Prevent violations through early detection and response. Catch potential offenders before they strike
CUSTOMER ID
Know your customers before they enter – delivering premium service that converts to sales
BIOMETRIC ACCESS
Streamline entry through speed gates with comprehensive visitor management and timekeeping
CASE NOT LISTED?
FRAUD MITIGATION
KNOW YOUR CUSTOMER
Receive instant security alerts when flagged individuals enter your premises, safeguarding your revenue and assets.
Gather demographic insights - including gender, age group, and emotional responses - enabling hyper-personalized customer engagement.








Ph.


Addr.
Encompass Business Park, 101 Rookwood Road, Yagoona, NSW 2199
Fax

LEGAL
(03)-9123-4296
(03)-9123-4297
info@rufen.com.au
Unit 20/16 Dunstans Ct, Thomastown VIC 3074